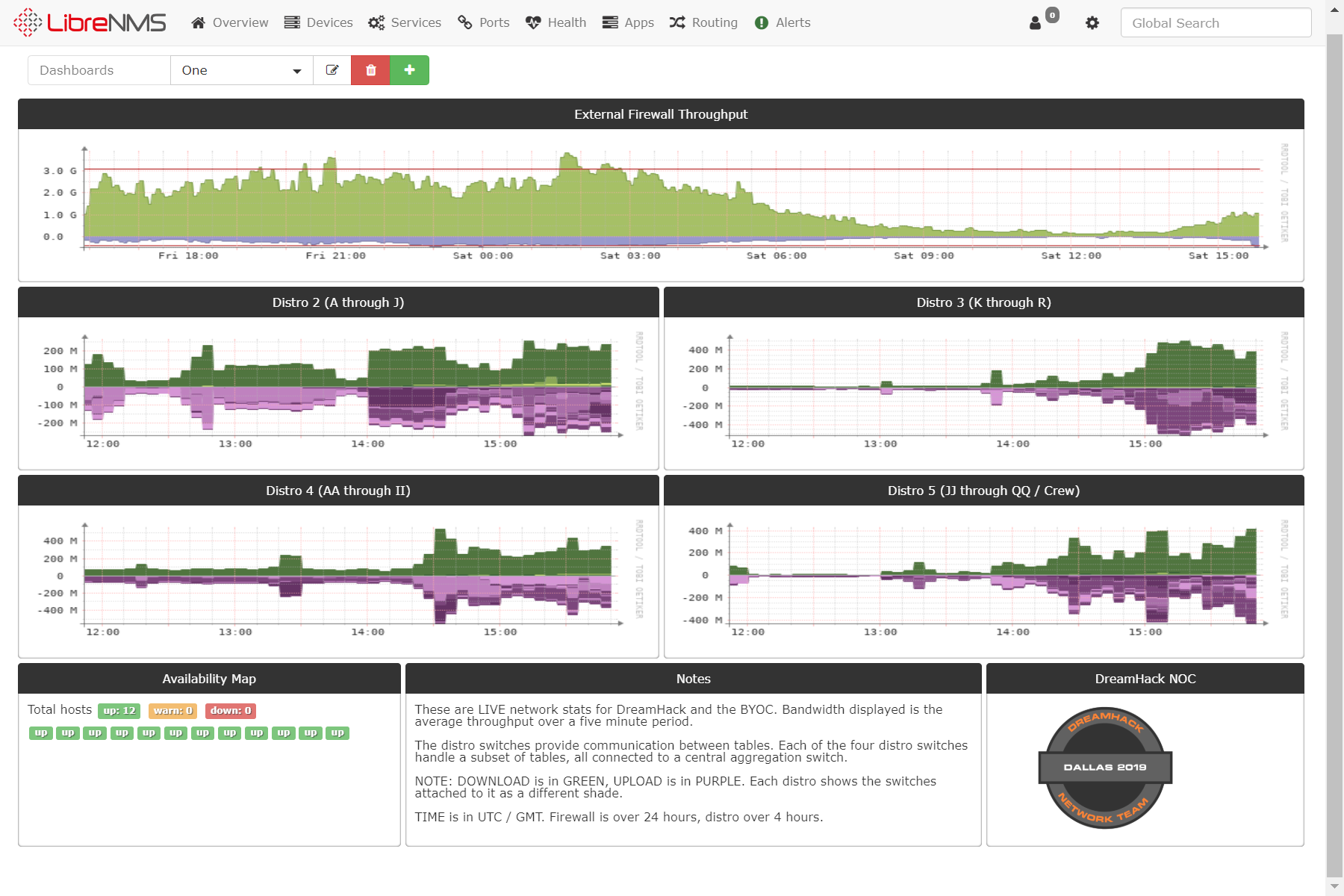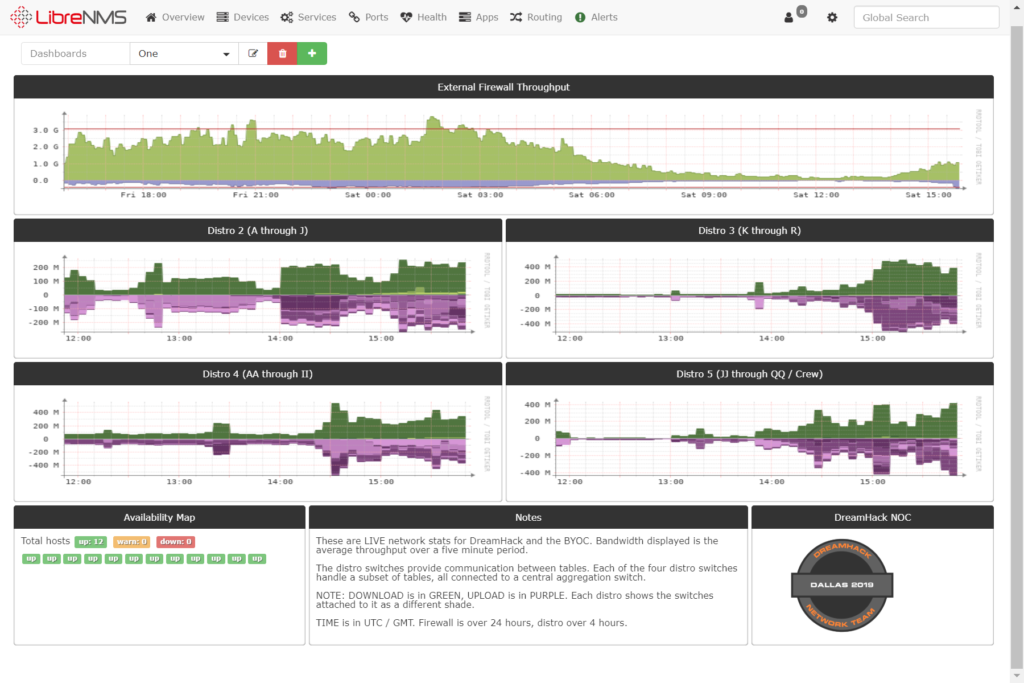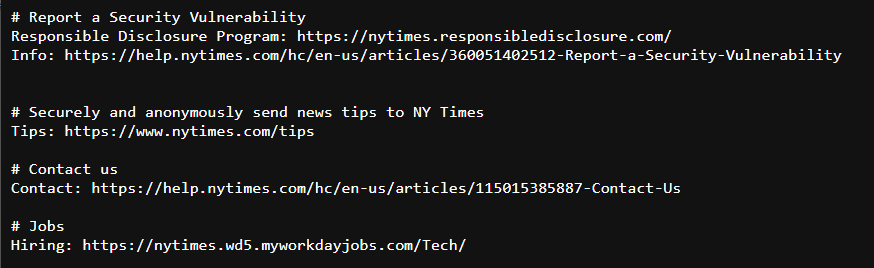
I finally did it — I achieved one of my lifelong goals: something I wrote was published on nytimes.com! Not exactly in the way you might imagine though, as the file that was published was a brand new security.txt file. You can read all about the concept and how it helps improve the security of The Times over at the Open blog, where the article I wrote was just published.